B implementing information systems to support better management decision making.
Electronic security systems include all of the following except which of the below.
Hackers may attempt to access sensitive information c.
Staffing and training employees to work in a technology driven environment b.
These measures include the following.
Data librarian in an information systems organization all of the following functions might logically report to the data center manager except.
Costs of internet commerce include all the following except.
The costs of security measures.
The phases of a large scale attack on an enterprise network or systems include the following except.
Surveillance infiltration execution.
C garnering more sales and profits than your competitors.
All of the following choices describe ways for a company to achieve a competitive advantage except.
Organizational change to a completely different way of doing business c.
General rules the security rule requires covered entities to maintain reasonable and appropriate administrative technical and physical safeguards for protecting e phi.
A very prominent example will be ssl tls a security protocol for communications over the internet that has been used in conjunction with a large number of internet protocols to ensure security.
Question 4 the security rule allows covered entities and business associates to take into account all of the following except.
Individuals or organizations may attempt to overload the system preventing legitimate customers from accessing the site.
Other ways to ensure information confidentiality include enforcing file permissions and access control list to restrict access to sensitive information.
The security rule calls this information electronic protected health information e phi.
In an information systems organization all of the following functions might logically report to the data center manager except.
Their size complexity and capabilities.
The risks to a business of internet commerce include all of the following except.
A producing a superior product and charging less than competitors.
High value information assets should be secured in a location with limited access.
Technological advances quickly antiquate hardware installations b.
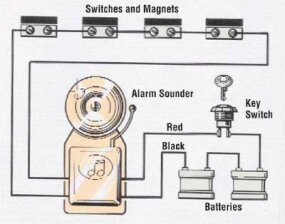
The earliest form of electronic keying was.
In a security classification system the level at which disclosure of information could cause exceptionally grave damage is.
Mailroom and other document preparation and handling costs are eliminated d.
T heir technical infrastructure hardware and software security capabilities.